Alternative Energy
Balancing Convenience and Security with Proximity-Based Technology

Consumers need to know that convenience often comes at the cost of security. A trend accelerated by the COVID-19 pandemic is the rising use of contactless mobile payments and proximity-based features. By 2020, 92.3 million U.S. consumers were using proximity-based mobile payments, with this number expected to encompass over half of all smartphone users by 2025. Features like AirDrop and NameDrop in iOS 17.1 epitomize this shift, offering seamless file and information sharing. Yet, many users remain unaware of the potential risks involved. As these technologies become ubiquitous, users face a dilemma: the ease of sharing versus the threat of cyber threats.
AirDrop, Apple’s renowned feature, and its counterparts like NameDrop have revolutionized how we transfer files between devices. But Luke Secrist, CEO of BuddoBot cautions against the hidden risks they could pose. “The trade-off between convenience and security is often overlooked,” Secrist points out. “Proximity-based tools, despite their intuitive ‘click-to-accept’ system, open up avenues for what we call ‘Drive-By Hacks.’”
These tools, when left active by default, can act as cell towers for cybercriminals. Secrist explains that these features, meant to simplify life, can inadvertently turn into gateways for hackers to access personal data or plant malicious files. The risk is especially among younger users, such as children and teenagers, who may lack the necessary skepticism when interacting with the prompts to deny or accept. “A simple tap to dismiss a notification can lead to unforeseen security breaches,” he adds, emphasizing the need for digital literacy and caution among younger demographics.
Secrist’s recommendation? Treat these convenient features with the same caution as other aspects of digital security. “Keep AirDrop and similar apps disabled when not in use. Turn them on only when you need to transfer files, and then switch them off immediately after,” he advises. This approach, while it may add a step or two to the file-sharing process, significantly lowers the risk of unwanted digital intrusions.
Drawing an analogy to everyday security measures, Secrist compares this practice to locking your car doors. “You wouldn’t leave them open on the off chance you’ll be back soon. Apply the same principle to your digital tools,” he suggests. In public spaces, where the likelihood of encountering a cyber threat is higher, this becomes even more crucial.
As new tech continually enters the market, understanding its potential drawbacks is key. “Awareness is your first line of defense in the cyber world,” states Luke Secrist. The significance of this statement was brought to life in a recent major cybersecurity event involving 23andMe. In 2023, the company suffered a significant data breach affecting 6.9 million users, primarily due to credential stuffing attacks. This incident not only led to the exposure of sensitive user data but also resulted in multiple class action lawsuits, demonstrating the devastating impact of cybersecurity vulnerabilities. Staying informed about the capabilities and risks of popular technologies can empower users to make smarter, safer decisions about their digital usage.
As we navigate the conveniences of modern tech, the insights from a cybersecurity expert like Secrist can make sure we’re all equipped with the necessary insights to make informed decisions. Balancing the ease of features like AirDrop with a mindful approach to security can help users enjoy the benefits of technology without falling prey to its pitfalls. In the fast-paced world of tech, staying informed and proactive is not just advisable – it’s essential for safeguarding our digital lives.
BuddoBot, a veteran and minority-owned business, specializes in authentic offensive cybersecurity. By emulating real-world attacks continuously, they go beyond traditional automated scanning and compliance. Their team of professional hackers and security experts craft custom solutions, utilizing true-to-life attack vectors to preemptively identify and mitigate potential security breaches.
-
 Press Release5 days ago
Press Release5 days agoClinical Trials Market Set for Robust Growth, Driven by Drug Development Surge and Digital Innovation
-

 Press Release6 days ago
Press Release6 days agoIndustrial Boiler Market Expected to Surpass USD 24.4 Billion by 2035 Amid Growing Demand for Energy Efficiency and Industrialization
-

 Business7 days ago
Business7 days agoHow Managed IT Solutions Help Small Teams Compete at Enterprise Scale
-
 Press Release6 days ago
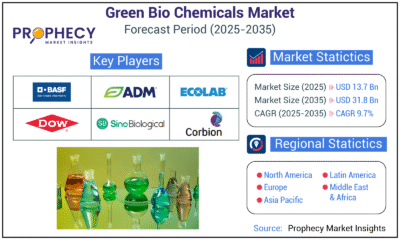
Press Release6 days agoGreen Bio Chemicals Market Poised for Sustainable Growth amidst Global Shift to Eco-Friendly Alternatives by 2035
-

 Press Release6 days ago
Press Release6 days agoFill-Finish Pharmaceutical Contract Manufacturing Market Expected to Flourish Amid Biopharmaceutical Boom and Global Outsourcing Trend by 2035
-
 Press Release6 days ago
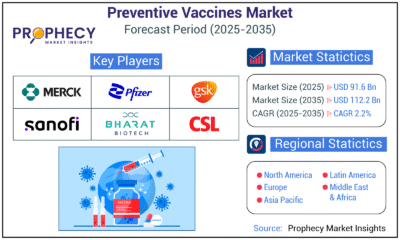
Press Release6 days agoPreventive Vaccines Market to Witness Strong Growth by 2035
-

 Press Release6 days ago
Press Release6 days agoPet Food Nutraceutical Market Set for Robust Expansion Amid Rising Demand for Pet Wellness by 2035
-

 Press Release5 days ago
Press Release5 days agoWaterproof Structural Adhesives Market: A Comprehensive Study Towards USD 10.3 Billion in 2035