Business
An Overview of Payment Card Industry Data Security Standard

The Payment Card Industry Data Security Standard (PCI DSS) applies to all entities processing payments. Companies must use security measures that ensure the integrity of cardholder data. Encryption, hashing, masking, and many others are included. The article covers fundamental principles and issues associated with PCI DSS and steps you can take to ensure your data is secure.
Protect cardholder data
Changing vendor default passwords is one way to secure your cardholder data. You must alter vendor-supplied passwords on all devices in your cardholder data environment, including your operating system, application, and network access points. All devices must be inventoried. Make an inventory of the hardware, software, and network components and describe their function and purpose. Default passwords on wireless access points and routers should also be changed.
Encrypting cardholder data is one of the best ways to protect the information you store, process, and transmit. Make sure to use strong encryption, trusted keys, and digital certificates. You should also install anti-virus and anti-malware software and implement physical security measures. By encrypting your cardholder data, you’ll ensure it’s protected from malicious software and attacks.
Encryption
The payment card industry data security standard (PCI DSS) is a standard for securing stored and transmitted cardholder data. It outlines a series of card companies’ requirements, including logging and monitoring requirements. These standards also dictate that stored cardholder data must be rendered unreadable if stolen or otherwise lost. By using a variety of methods, a company can meet these standards.
The PCI DSS is a standard set of security requirements that all organizations handling credit cards must meet. Four major credit card companies developed it to improve control over cardholder data and prevent fraud. It specifies six primary objectives for organizations that process credit cards.
Hashing
Companies using hashing to protect their cardholder data is unreadable and is required by PCI DSS. Hashing renders unreadable and is required by PCI DSS. While the security properties of hashing are not immediately apparent, many applications of card hashing remain flawed.
PCI DSS requires that hashing PAN data be one-way and have strong cryptography. Moreover, it requires that a salt accompanies the hash to make it more difficult for someone to recover the PAN. However, simple soups do not meet the PCI DSS requirement. Therefore, these methods are not effective in preventing PAN theft. In addition, hashing is the wrong choice for storing PANs on long-term systems.
Masking
Companies that store sensitive information has a duty of care to protect it. These laws require them to make use of effective data security measures. Masking is one such way to protect sensitive data. A software can scan unexpected locations for sensitive data and mask and remediate it. For example, a company can use masking to ensure that its output data is unreadable.
Data solution uses proven data transformation techniques to replace actual data with fictitious data. It can mask data in a single database or across several related systems and applications. It also supports date aging and concatenation. Masking ensures privacy while protecting your customers’ sensitive information. The data privacy solution can de-identify and mask data from multiple sources for complete confidentiality and security.
Truncation
Truncation is a data modification acceptable in the Payment Card Industry Data Security Standard (PCI-DSS). This makes it harder for criminals to obtain information stored on the payment card by truncating the PAN. However, the requirement does not apply to handwritten receipts or manual imprinters. To comply with the PCI-DSS, developers of payment solutions must understand the rules surrounding truncation.
Truncation is a permanent process. It differs from PCI-DSS requirement 3.3, which speaks to the temporary masking of data displayed. Several methods are acceptable.
Logging
PCI security guidance requires organizations to maintain a log of security events for a minimum of 90 days. It also mandates the creation and retention of records and a daily review of logs. Therefore, organizations should develop a logging policy covering these tasks, which may be carried out manually or automatically. A logging approach makes it easier to become compliant, validate, and keep it. In the age of compliance, log management has become a requirement.
Keeping records of system access is an essential part of PCI DSS compliance. Logging can help prevent fraudulent activity by ensuring that cardholder data is not leaked. This information can be stolen when it reaches unauthorized parties. A PCI DSS-compliant organization will log access to cardholder data. This process is required to ensure the security of cardholder data. This can be done through multiple software products, multiple locations, a few employees, and regular vulnerability testing.
-

 Press Release5 days ago
Press Release5 days agoBellarium ($BEL) Price Prediction: Could It Hit $5 by 2026?
-
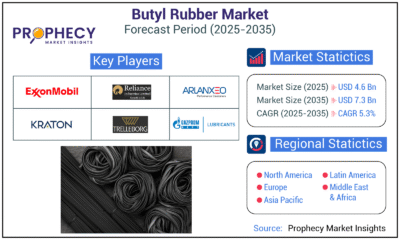
 Press Release2 days ago
Press Release2 days agoClinical Trials Market Set for Robust Growth, Driven by Drug Development Surge and Digital Innovation
-

 Press Release3 days ago
Press Release3 days agoIndustrial Boiler Market Expected to Surpass USD 24.4 Billion by 2035 Amid Growing Demand for Energy Efficiency and Industrialization
-
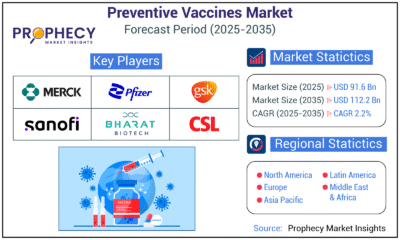
 Press Release3 days ago
Press Release3 days agoPreventive Vaccines Market to Witness Strong Growth by 2035
-

 Business4 days ago
Business4 days agoHow Managed IT Solutions Help Small Teams Compete at Enterprise Scale
-
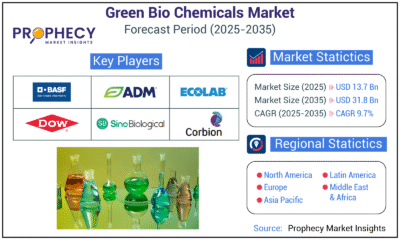
 Press Release3 days ago
Press Release3 days agoGreen Bio Chemicals Market Poised for Sustainable Growth amidst Global Shift to Eco-Friendly Alternatives by 2035
-

 Press Release3 days ago
Press Release3 days agoFill-Finish Pharmaceutical Contract Manufacturing Market Expected to Flourish Amid Biopharmaceutical Boom and Global Outsourcing Trend by 2035
-

 Press Release3 days ago
Press Release3 days agoPet Food Nutraceutical Market Set for Robust Expansion Amid Rising Demand for Pet Wellness by 2035