Technology
Navigating the Digital Labyrinth: The Evolution of Identity Protection

The digital age has ushered in an era of unprecedented connectivity and convenience. However, it has also given rise to a nefarious byproduct: identity theft. This phenomenon, while not entirely new, has morphed with the evolution of technology, presenting ever-evolving challenges to individuals and society. Identity theft protection, once a niche concern, has now become a critical aspect of our digital lives, necessitating a deeper understanding of its trajectory and the technologies that shape it.
Historically, identity theft was a crime of opportunity, limited by the physical constraints of accessing personal documents or intercepting snail mail. The advent of the internet and digital data storage transformed this landscape, offering both new opportunities for criminals and novel solutions for protection. From rudimentary methods to sophisticated digital tools, the journey of identity theft protection is a tale of cat-and-mouse between criminals and protectors.
Today, identity theft protection is not just a personal concern but a global imperative. As our lives become increasingly digitized, from social media footprints to online banking, the need for robust protection mechanisms has never been more critical. This article explores three key dimensions of identity theft protection: its historical context, the current state of affairs, and the future challenges and opportunities presented by emerging technologies.
The Evolution of Identity Theft
The history of identity theft is intrinsically linked to the history of personal data. In the pre-internet era, identity theft involved physical theft of documents or impersonation. The shift to digital storage and the proliferation of online transactions in the late 20th century marked a significant turning point. Cybercriminals found new avenues to exploit, from hacking into databases to phishing scams, necessitating a paradigm shift in protection strategies.
This evolution spurred the development of specialized services, offering monitoring and alert systems to detect potential breaches. Initially focusing on credit and financial data, these services expanded to include a wide range of personal information. The rise of social media and the ubiquity of smartphones further complicated the landscape, introducing new vulnerabilities and expanding the frontier for identity thieves.
The complexity of modern identity theft calls for sophisticated solutions. Protection services now employ advanced technologies like artificial intelligence and machine learning to predict and prevent identity theft. These tools can analyze vast amounts of data, recognize patterns, and alert users to suspicious activities, offering a proactive approach to protection.
The Present State of Identity Protection
Currently, identity theft protection is a multifaceted field, blending technology, psychology, and legal frameworks. The diversity of threats, from simple credit card fraud to complex identity cloning, requires a comprehensive approach to protection. Services now offer a range of features, including credit monitoring, dark web surveillance, and recovery assistance, to provide an all-encompassing safety net.
One of the critical aspects of modern identity protection is the focus on real-time alerts and rapid response. Quick detection of fraud can significantly mitigate the damage, making speed a crucial factor. Additionally, the integration of cybersecurity tools like VPNs, antivirus software, and password managers has become a standard practice, reflecting the interconnected nature of identity theft and online security.
Education and awareness are also crucial components of contemporary identity protection services. With the majority of identity theft incidents stemming from user behavior, such as weak passwords or falling for phishing scams, educating the public on best practices is as vital as technological solutions. This holistic approach, combining prevention, monitoring, and recovery, defines the current state of identity theft protection.
Looking Ahead: Future Challenges and Innovations
The future of identity theft protection is poised at an interesting juncture, with emerging technologies presenting both challenges and solutions. The proliferation of IoT devices and the advent of technologies like blockchain and biometrics are reshaping the landscape. These technologies promise more secure and unique identification methods, potentially reducing the risk of identity theft.
However, the same technologies also present new vulnerabilities. The increasing number of connected devices expands the attack surface for cybercriminals. Moreover, the sophistication of AI and machine learning tools, while beneficial for protection, can also be leveraged by criminals to devise more advanced attack strategies.
The future of identity protection will likely see a greater emphasis on predictive and preventive measures. Leveraging big data and AI for behavioral analysis and anomaly detection could preempt many identity theft attempts. Additionally, regulatory frameworks and global collaboration will play a crucial role in shaping effective and universally applicable protection strategies.
Conclusion
The journey of identity theft protection is a reflection of our evolving digital society. From simple beginnings to a complex web of technologies and strategies, this field has continuously adapted to the changing landscape of threats. The future, while presenting exciting possibilities, also warns of sophisticated challenges requiring innovative solutions.
As we navigate this digital labyrinth, the importance of vigilance, education, and adaptation cannot be overstated. Individuals, organizations, and governments must collaborate to foster a secure digital environment.
-

 Press Release3 days ago
Press Release3 days agoNura Labs Files Revolutionary Patent: AI-Powered Wallet Solves the $180 Billion Crypto Staking Complexity Crisis
-
 Press Release1 day ago
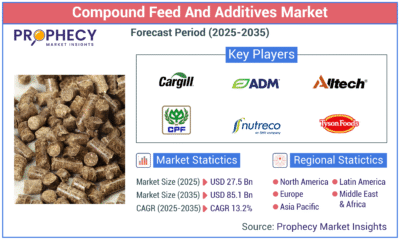
Press Release1 day agoGlobal Compound Feeds and Additives Industry Report: Market Expansion and Competitive Insights to 2035
-

 Technology1 day ago
Technology1 day agoWhat to Know Before Switching Cell Phone Network Services in 2025