Blockchain Technology
Blockchain Security Solutions: Protecting Digital Assets

Blockchain technology is becoming increasingly important in our digital world, providing a secure way to manage and store information. However, with this rise in popularity comes the need for strong security measures to protect digital assets from threats. This article explores various aspects of blockchain security solutions, focusing on how to keep digital assets safe.
Key Takeaways
- Blockchain security is vital for protecting digital assets from theft and hacking.
- Cryptography plays a key role in ensuring the safety of blockchain systems.
- Smart contracts can have weaknesses, so it’s essential to follow best practises for their security.
- Decentralised Finance (DeFi) platforms face unique risks that require specific security measures.
- Future advancements in blockchain security will be crucial in tackling upcoming challenges.
Understanding Blockchain Security Solutions
Key Concepts in Blockchain Security
Blockchain security is a comprehensive risk management process that involves using various cybersecurity frameworks and testing methods. It ensures that the data stored on the blockchain is safe from attacks and unauthorised access. Key concepts include:
- Decentralisation: Reduces the risk of a single point of failure.
- Transparency: All transactions are visible, making it easier to detect fraud.
- Immutability: Once data is added, it cannot be changed, ensuring integrity.
Importance of Blockchain Security
The significance of blockchain security cannot be overstated. It protects digital assets and builds trust among users. Here are some reasons why it is crucial:
- Protects assets: Safeguards cryptocurrencies and sensitive information.
- Maintains trust: Users are more likely to engage with secure platforms.
- Prevents fraud: Reduces the chances of hacking and scams.
Common Threats to Blockchain Systems
Despite its advantages, blockchain systems face several threats. Some common ones include:
- 51% attacks: When a group gains control of the majority of the network, they can manipulate transactions.
- Phishing attacks: Fraudsters trick users into revealing their private keys.
- Smart contract vulnerabilities: Flaws in smart contracts can be exploited, leading to financial losses.
Blockchain security is essential for the future of digital transactions. Without it, the entire system could be at risk.
Cryptographic Techniques in Blockchain Security
Role of Cryptography in Blockchain
Cryptography is essential in blockchain technology. It ensures that data is secure and only accessible to those who are allowed to see it. This helps protect digital assets from unauthorised access and tampering. The main roles of cryptography in blockchain include:
- Data Integrity: Ensures that the data has not been altered.
- Authentication: Confirms the identity of users and devices.
- Confidentiality: Keeps sensitive information private.
Types of Cryptographic Algorithms Used
There are several types of cryptographic algorithms used in blockchain. Here are some of the most common ones:
| Algorithm Type | Description |
|---|---|
| Hash Functions | Converts data into a fixed-size string of characters, which is unique to the original data. |
| Symmetric Encryption | Uses the same key for both encryption and decryption. |
| Asymmetric Encryption | Uses a pair of keys: a public key and a private key. |
Benefits of Cryptographic Security
Using cryptography in blockchain offers many advantages:
- Enhanced Security: Protects against hacking and fraud.
- Trust: Builds confidence among users by ensuring data is secure.
- Transparency: Allows users to verify transactions without revealing personal information.
Cryptography is the backbone of blockchain security, making it a vital part of protecting digital assets.
Smart Contract Security Measures
Vulnerabilities in Smart Contracts
Smart contracts are not without their flaws. Some common vulnerabilities include:
- Reentrancy attacks: This occurs when a contract calls another contract and the second contract calls back into the first before it finishes executing.
- Integer overflow/underflow: This happens when calculations exceed the maximum or minimum limit of a number.
- Gas limit and loops: If a contract has loops that run too long, it can run out of gas and fail.
Best Practises for Smart Contract Security
To ensure the safety of smart contracts, developers should follow these best practises:
- Code audits: Regularly review the code for potential vulnerabilities.
- Testing: Use automated testing tools to check for errors before deployment.
- Upgradable contracts: Design contracts that can be updated to fix issues without losing data.
Tools for Auditing Smart Contracts
There are several tools available to help audit smart contracts:
- MythX: A security analysis tool that checks for vulnerabilities.
- Slither: A static analysis tool that helps find bugs in Solidity code.
- Oyente: A tool that detects security issues in Ethereum smart contracts.
Smart contracts are a powerful tool, but they require careful attention to security to protect digital assets.
Decentralised Finance (DeFi) Security

Decentralised Finance, or DeFi, is changing how we think about money and finance. However, with this change comes new risks that need to be managed.
Risks in DeFi Platforms
- Smart contract vulnerabilities: Bugs in the code can lead to loss of funds.
- Market manipulation: Bad actors can influence prices unfairly.
- Liquidity risks: Sudden changes in market conditions can cause problems for users.
Security Protocols for DeFi
To protect users and their assets, DeFi platforms often use several security measures:
- Auditing smart contracts: Regular checks to find and fix issues.
- Multi-signature wallets: Requiring multiple approvals for transactions.
- Insurance protocols: Offering coverage against losses due to hacks.
Case Studies of DeFi Security Breaches
Several incidents have highlighted the need for better security in DeFi:
- The DAO hack: A major breach that led to a significant loss of funds.
- Poly Network hack: Over $600 million was stolen, raising alarms in the community.
- Bzx protocol incident: Exploits that caused users to lose money.
In the world of DeFi, security is paramount. Without it, users may lose trust and funds, which can halt the growth of this innovative sector.
By understanding these risks and implementing strong security measures, DeFi can continue to thrive while protecting users’ digital assets.
Blockchain Security for Enterprises
Enterprise-Level Security Challenges
Businesses face several security challenges when implementing blockchain technology. These include:
- Data privacy concerns, as sensitive information is often stored on a public ledger.
- The need for interoperability between different blockchain systems.
- Ensuring compliance with regulatory standards that vary by region.
Implementing Blockchain Security Solutions in Business
To effectively secure blockchain systems, enterprises should consider the following steps:
- Conduct a risk assessment to identify potential vulnerabilities.
- Develop a security policy that outlines best practises and protocols.
- Train employees on security measures and the importance of safeguarding digital assets.
Compliance and Regulatory Considerations
Adhering to regulations is crucial for businesses using blockchain. Key points include:
- Understanding local and international laws regarding data protection.
- Regularly updating security measures to comply with changing regulations.
- Engaging with legal experts to ensure all practises are legally sound.
Blockchain technology can greatly enhance security, but it requires careful planning and execution to protect digital assets effectively. Understanding the risks and implementing robust solutions is essential for success.
Identity and Access Management in Blockchain
Managing Digital Identities
In the world of blockchain, managing digital identities is crucial. Each user needs a unique identity to interact securely. This can be achieved through:
- Public and private keys: These are essential for secure transactions.
- Decentralised identifiers (DIDs): These allow users to control their own identities without relying on a central authority.
- Self-sovereign identity: This concept gives users full control over their personal data.
Access Control Mechanisms
Access control is vital to ensure that only the right people can access certain information. Common mechanisms include:
- Role-based access control (RBAC): Users are assigned roles that determine their access level.
- Attribute-based access control (ABAC): Access is granted based on user attributes and environmental conditions.
- Multi-factor authentication (MFA): This adds an extra layer of security by requiring multiple forms of verification.
Preventing Unauthorised Access
To keep blockchain systems safe, it’s important to prevent unauthorised access. Here are some strategies:
- Regular audits: Check access logs to identify any suspicious activity.
- Encryption: Protect sensitive data to make it unreadable to unauthorised users.
- User education: Teach users about security best practises to avoid phishing and other attacks.
Managing identities and access in blockchain is not just about technology; it’s about building trust and ensuring security for all users.
| Access Control Type | Description | Pros |
|---|---|---|
| Role-based | Assigns access based on user roles | Simple to manage |
| Attribute-based | Grants access based on user attributes | Flexible and dynamic |
| Multi-factor | Requires multiple verifications | Highly secure |
Consensus Mechanisms and Security
Types of Consensus Mechanisms
There are several types of consensus mechanisms used in blockchain technology. Here are the most common ones:
- Proof of Work (PoW): This method requires participants to solve complex mathematical problems to validate transactions.
- Proof of Stake (PoS): In this system, validators are chosen based on the number of coins they hold and are willing to "stake" as collateral.
- Delegated Proof of Stake (DPoS): This is a variation of PoS where stakeholders elect delegates to validate transactions on their behalf.
Security Implications of Different Mechanisms
Each consensus mechanism has its own security features and weaknesses. Here are some key points:
- PoW is often seen as secure but can be vulnerable to attacks if a single entity controls a large portion of the mining power.
- PoS can be more energy-efficient but may lead to centralisation if a few holders control most of the stakes.
- DPoS can improve transaction speed but may expose the system to risks if delegates are not trustworthy.
Improving Consensus Security
To enhance the security of consensus mechanisms, consider the following strategies:
- Regularly update the protocol to fix vulnerabilities.
- Implement multi-signature requirements for critical transactions.
- Conduct audits and stress tests to identify weaknesses.
In summary, the choice of consensus mechanism plays a crucial role in the overall security of a blockchain system. Understanding the strengths and weaknesses of each method is essential for protecting digital assets effectively.
The security of blockchain systems is vital, especially in areas like asset archives where the integrity of transactions is paramount. By choosing the right consensus mechanism and implementing robust security measures, we can safeguard our digital assets against potential threats.
Blockchain Security Tools and Technologies

Popular Blockchain Security Tools
There are several tools available to help secure blockchain systems. Some of the most popular include:
- MythX: A tool for detecting vulnerabilities in smart contracts.
- Slither: A static analysis tool that helps find bugs in Solidity code.
- Truffle Suite: A development environment that includes testing and security features.
Emerging Technologies in Blockchain Security
New technologies are constantly being developed to enhance blockchain security. Some of these include:
- Zero-Knowledge Proofs: Allowing one party to prove to another that a statement is true without revealing any information.
- Multi-Signature Wallets: Requiring multiple approvals before a transaction can be made, adding an extra layer of security.
- Decentralised Identity Solutions: Helping users manage their identities securely on the blockchain.
Evaluating Security Tools
When choosing a security tool for blockchain, consider the following:
- Ease of Use: Is the tool user-friendly?
- Effectiveness: Does it effectively find and fix vulnerabilities?
- Community Support: Is there a strong community or support system?
Blockchain security tools are essential for protecting digital assets and ensuring the integrity of transactions. They help in identifying vulnerabilities and preventing attacks.
In summary, using the right tools and technologies is crucial for maintaining a secure blockchain environment. By staying updated with the latest advancements, businesses can better protect their digital assets and mitigate risks.
Incident Response and Recovery in Blockchain
Preparing for Security Incidents
To effectively handle security incidents in blockchain systems, organisations must be well-prepared. Here are some key steps to consider:
- Develop a response plan: Create a clear plan that outlines how to respond to different types of incidents.
- Train your team: Ensure that all team members understand their roles in the event of a security breach.
- Regularly test your plan: Conduct drills to ensure that everyone knows what to do when an incident occurs.
Steps to Take After a Breach
When a security breach happens, it’s crucial to act quickly. Here are the steps to follow:
- Identify the breach: Determine how the breach occurred and what data was affected.
- Contain the damage: Take immediate action to limit further damage to the system.
- Notify stakeholders: Inform affected parties, including users and regulatory bodies, about the breach.
Recovery Strategies for Blockchain Systems
After addressing the immediate threat, focus on recovery. Here are some strategies:
- Conduct a thorough investigation: Understand the full impact of the breach and gather evidence.
- Restore systems: Bring systems back online safely, ensuring they are secure before doing so.
- Review and improve security measures: Learn from the incident to strengthen security protocols.
A strong incident response plan is essential for protecting digital assets. It helps organisations respond effectively to breaches and recover quickly.
In summary, being prepared for security incidents, knowing the steps to take after a breach, and having solid recovery strategies are vital for maintaining the integrity of blockchain systems. By focusing on these areas, organisations can better protect their digital assets and ensure a swift recovery from any incidents.
Future Trends in Blockchain Security Solutions
Innovations in Blockchain Security
The future of blockchain security is bright, with new technologies emerging to enhance protection. Innovations such as artificial intelligence and machine learning are being integrated to predict and prevent security threats. These technologies can analyse patterns and detect anomalies in real-time, making them essential for safeguarding digital assets.
Predictions for Blockchain Security
Experts believe that the following trends will shape the future of blockchain security:
- Increased Regulation: Governments are likely to introduce stricter regulations to protect users and ensure compliance.
- Enhanced User Education: As threats evolve, educating users about security practises will become crucial.
- Decentralised Identity Solutions: These will help manage digital identities more securely, reducing the risk of fraud.
Challenges Ahead for Blockchain Security
Despite advancements, several challenges remain:
- Scalability Issues: As blockchain networks grow, maintaining security without sacrificing speed will be a challenge.
- Evolving Threats: Cybercriminals are constantly finding new ways to exploit vulnerabilities.
- Integration with Legacy Systems: Merging blockchain with existing systems can create security gaps.
The landscape of blockchain security is ever-changing, and staying ahead of threats requires constant vigilance and adaptation.
In summary, the future of blockchain security will be defined by innovative solutions, increased regulations, and ongoing challenges that need to be addressed to protect digital assets effectively.
Blockchain Security in Cryptocurrency Exchanges
Security Risks in Exchanges
Cryptocurrency exchanges face various security risks that can lead to significant losses. Some of the most common risks include:
- Hacking attempts: Cybercriminals often target exchanges to steal funds.
- Phishing scams: Users may be tricked into giving away their login details.
- Insider threats: Employees with access to sensitive information can pose risks.
Protecting User Funds
To ensure the safety of user funds, exchanges should implement several key measures:
- Cold storage: Keeping the majority of funds offline to prevent hacking.
- Two-factor authentication (2FA): Adding an extra layer of security for user accounts.
- Regular security audits: Checking systems for vulnerabilities regularly.
Regulatory Measures for Exchange Security
Governments are increasingly focusing on the security of cryptocurrency exchanges. Some important regulatory measures include:
- Licencing requirements: Exchanges must obtain licences to operate legally.
- Anti-money laundering (AML) policies: Ensuring that exchanges monitor transactions for suspicious activity.
- User data protection: Regulations to safeguard personal information of users.
In the world of cryptocurrency, security is paramount. Without proper measures, exchanges can become easy targets for criminals, leading to devastating losses for users and the platform itself.
Conclusion
In summary, securing digital assets through blockchain technology is crucial in today’s world. As we have seen, various solutions exist to protect these assets from threats. By using strong encryption, smart contracts, and regular updates, individuals and businesses can keep their digital valuables safe. It’s important to stay informed about the latest security measures and to adopt best practises. With the right tools and knowledge, we can ensure that our digital future remains secure and trustworthy.
-

 Press Release5 days ago
Press Release5 days agoBellarium ($BEL) Price Prediction: Could It Hit $5 by 2026?
-
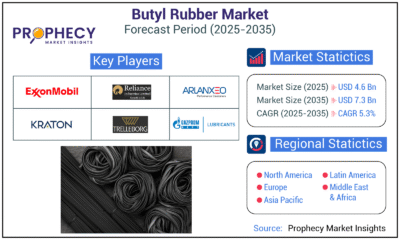
 Press Release2 days ago
Press Release2 days agoClinical Trials Market Set for Robust Growth, Driven by Drug Development Surge and Digital Innovation
-

 Business4 days ago
Business4 days agoHow Managed IT Solutions Help Small Teams Compete at Enterprise Scale
-

 Press Release3 days ago
Press Release3 days agoIndustrial Boiler Market Expected to Surpass USD 24.4 Billion by 2035 Amid Growing Demand for Energy Efficiency and Industrialization
-
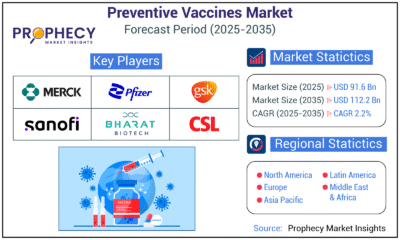
 Press Release3 days ago
Press Release3 days agoPreventive Vaccines Market to Witness Strong Growth by 2035
-
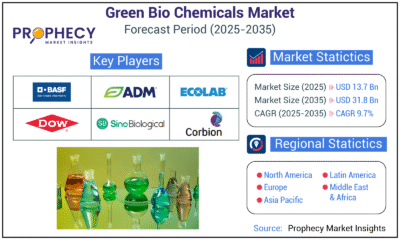
 Press Release3 days ago
Press Release3 days agoGreen Bio Chemicals Market Poised for Sustainable Growth amidst Global Shift to Eco-Friendly Alternatives by 2035
-

 Press Release3 days ago
Press Release3 days agoFill-Finish Pharmaceutical Contract Manufacturing Market Expected to Flourish Amid Biopharmaceutical Boom and Global Outsourcing Trend by 2035
-

 Press Release3 days ago
Press Release3 days agoPet Food Nutraceutical Market Set for Robust Expansion Amid Rising Demand for Pet Wellness by 2035