Business
Access Control Services for Enhanced Security: A Comprehensive Guide

In today’s rapidly evolving digital landscape, security concerns continue to escalate. Businesses and individuals alike face increasing threats to their sensitive information and assets. To combat these risks effectively, the implementation of robust access control services has become paramount. This article aims to guide you through the intricate realm of access control, elucidating its significance, types, components, benefits, challenges, best practices, and more.
Access control services encompass an array of techniques and systems designed to manage and monitor access to resources, physical locations, and data within an organization. These services enable the regulation of who can enter a particular area, use specific systems, or access particular information. In essence, access control ensures that only authorized personnel can access designated resources, thereby fortifying security.
Understanding the Importance of Access Control
Security breaches can lead to devastating consequences, including data theft, unauthorized access, and operational disruptions. Access control mitigates these risks by providing a layered defense mechanism, bolstering the overall security posture of an entity. Whether it’s restricting entry to a restricted area or safeguarding critical digital assets, access control serves as a pivotal tool in fortifying security measures.
Types of Access Control Services
Physical Access Control: This type of access control regulates entry to physical spaces through methods like key cards and biometric scanners, providing a seamless yet secure means for authorized personnel to access designated areas. The inclusion of security personnel adds an extra layer of vigilance and immediate response capability to enhance overall physical security.
Logical Access Control: Centered on digital systems, logical access control governs entry to networks, databases, and applications using security measures such as passwords, two-factor authentication, and encryption. This ensures that only authorized individuals can access and interact with sensitive digital assets, fortifying the integrity and confidentiality of digital information.
Components of Access Control Systems
Access control systems consist of diverse elements, incorporating authentication methods such as passwords, biometrics, and tokens. These methods validate the identity of individuals seeking access. In tandem, authorization techniques define the specific resources that an authenticated individual can access, meticulously aligning with predetermined permissions to uphold a secure and controlled environment.
Benefits of Implementing Access Control Services
The implementation of robust access control yields multifaceted advantages, encompassing heightened security, adherence to regulatory compliance, improved operational efficiency, and a streamlined user experience. This comprehensive approach not only safeguards sensitive information but also fosters a secure and efficient organizational ecosystem for both users and administrators alike.
Factors to Consider When Choosing Access Control Services
In the choice of access control services, careful evaluation of factors such as scalability, integration capabilities, user-friendliness, and compliance requirements is imperative. A meticulous assessment of these elements ensures that the selected solution aligns seamlessly with the organization’s current needs while allowing for adaptability to future growth, integration with existing systems, ease of use, and compliance with regulatory standards.
Common Challenges in Access Control Systems
Despite their significance, access control systems face challenges, including the complexity of implementation, resistance from users, and the dynamic nature of evolving threat landscapes. Navigating these challenges demands a strategic and adaptive approach to ensure the effectiveness and acceptance of access control measures within the organization.
Best Practices for Implementing Access Control
To maximize the effectiveness of access control services, organizations should adhere to best practices, incorporating regular audits to assess system integrity, comprehensive training programs to empower users with security protocols, and adopting a layered security approach. This multifaceted strategy not only fortifies the access control infrastructure but also proactively addresses potential vulnerabilities, fostering a resilient and proactive security posture.
Integration of Access Control Services with Other Security Measures
For a comprehensive security infrastructure, access control systems should seamlessly integrate with other security measures, such as intrusion detection systems and surveillance cameras. This synergy ensures a cohesive and responsive security ecosystem, where access control complements and enhances the overall surveillance and threat detection capabilities of the organization.
Future Trends in Access Control Services
The trajectory of access control services points towards future advancements, anticipating innovations in biometrics, authentication driven by artificial intelligence, and the emergence of decentralized access control models. These developments signify a shift towards more sophisticated and adaptive security paradigms, leveraging cutting-edge technologies to address the evolving challenges of securing digital and physical spaces.
Case Studies Highlighting Successful Access Control Implementations
Real-world examples showcasing successful implementations of access control services serve as compelling evidence, emphasizing their efficacy in thwarting security threats and ensuring compliance. These case studies not only validate the practical benefits of access control but also provide tangible insights into how organizations have successfully navigated and addressed security challenges in diverse contexts.
Steps to Enhance Security through Access Control Services
Guidelines for optimizing the effectiveness of access control services include regular system updates to address emerging threats, conducting comprehensive risk assessments to identify vulnerabilities, and fostering a security-centric culture within the organization. By following these proactive measures, businesses can ensure that their access control systems remain robust and adaptive in the face of evolving security landscapes, ultimately enhancing overall organizational resilience.
Cost Considerations and ROI in Access Control
Assessing the costs associated with implementing access control services is crucial, necessitating a thorough examination of both initial investments and ongoing expenses. Simultaneously, evaluating the return on investment (ROI) becomes pivotal in justifying security expenditure. This strategic financial approach ensures that the implementation of access control not only fortifies security but also proves to be a prudent and valuable investment for the long-term resilience of the organization.
Maintaining and Updating Access Control Systems
Regular maintenance, updates, and timely application of patches are of paramount importance to ensure the continued efficacy of access control systems against evolving threats. This proactive approach safeguards against vulnerabilities, enhances system resilience, and maintains the integrity of the access control infrastructure, thereby upholding the overall security posture of the organization.
Conclusion
In conclusion, navigating the realm of access control services is pivotal for fortifying security measures. Through a comprehensive understanding of its types, components, benefits, challenges, and best practices, both individuals and organizations can strategically fortify their defense against an ever-evolving threat landscape. Embracing the multifaceted aspects of access control ensures a robust security posture that adapts to emerging challenges, ultimately safeguarding valuable assets and information.
-

 Destinations4 days ago
Destinations4 days agoSave Money in London: Insider Tips for Budget Travellers
-

 USA News3 days ago
USA News3 days agoWhat Is The Current Us Elections Rating And Who Is Leading The Polls?
-
 Technology5 days ago
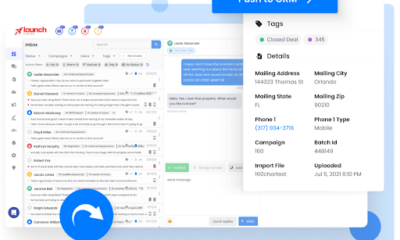
Technology5 days agoEnhancing Lead Management and Text Marketing with Launch Control’s All-in-One CRM
-

 Europe News3 days ago
Europe News3 days agoSee Rome on a Budget: History and Culture Without the Cost
-

 Travel3 days ago
Travel3 days agoHow to Make Friends in Southeast Asia Hostels: A Guide for Solo Travellers
-

 Climate Change3 days ago
Climate Change3 days agoCuba Faces Nationwide Power Grid Collapse Amidst Ongoing Crisis
-

 Travel3 days ago
Travel3 days agoSafe Travel in Mexico: Tips for a Hassle-Free Trip
-

 Destinations4 days ago
Destinations4 days agoArgentina Travel Guide: Tango, Wine, and Natural Wonders